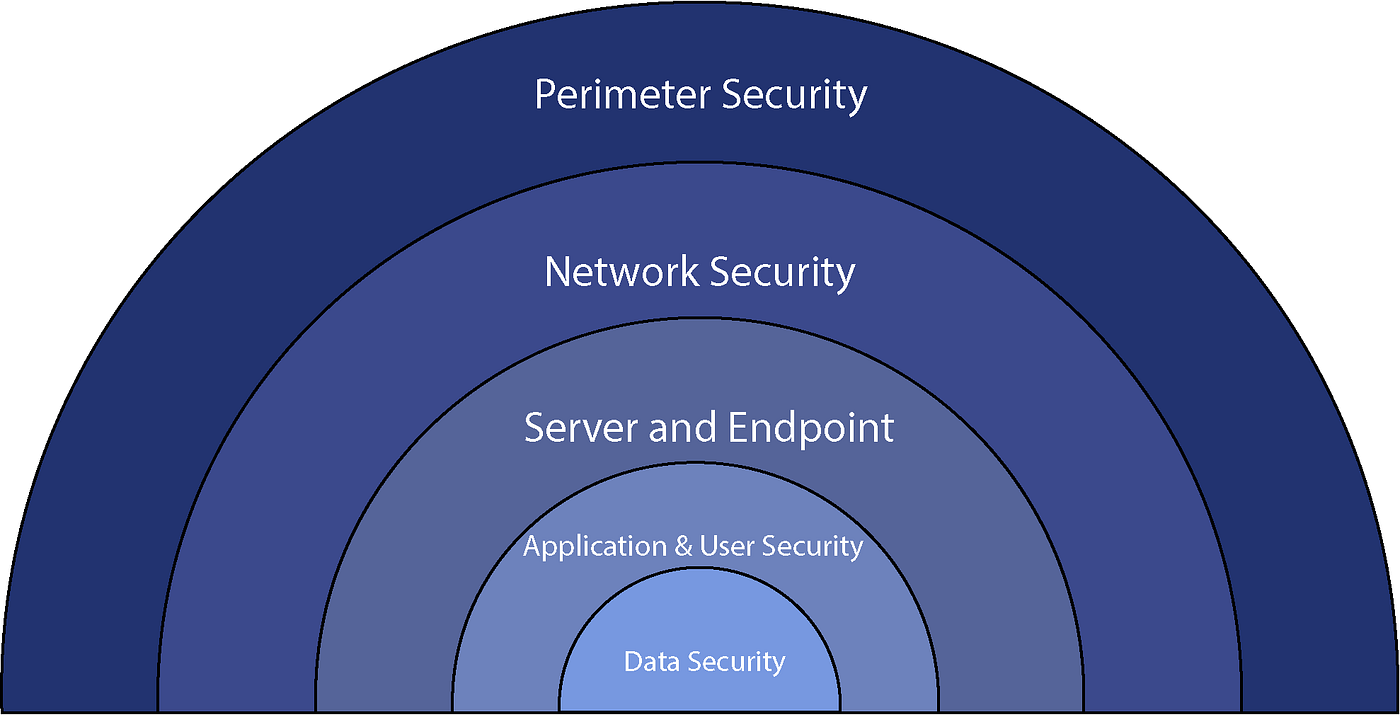
How Backup and Disaster Recovery Protects Businesses
Backup and disaster recovery are crucial for safeguarding businesses, particularly small & medium-sized, from the serious consequences of data loss and operational disruptions. Whether caused by human error, cyberattacks, or natural disasters, the fallout can include costly downtime, reputation damage, regulatory penalties, and even business closure. Prioritizing a comprehensive solution ensures secure data backup, rapid recovery, and uninterrupted operations, often leveraging cloud technology. Key terms like Recovery Time Objective (RTO) and Recovery Point Objective (RPO) measure downtime and potential data loss. Implementing effective backup and disaster recovery strategies offer benefits such as protection from natural disasters, cyberattack resilience, data security, quick recovery, error mitigation, and system failure preparedness, all contributing to business resilience and peace of mind.